Crown Street, Wollongong, 2500
Bridging the Gap: Tackling Persistent IoT Challenges in the Cloud Era
1. INTRODUCTION
The Internet of Things (IoT) has gained recognition as one of the prominent technological advancements of the 21st century, which brought the ubiquitous connectivity and intelligent automation into a reality. IoT, while reshaping every facet of modern life, is also serving a plethora of domains and fields. The rise of powerful cloud computing services like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform etc., has fueled the transformation of IoT which leverages key capabilities of cloud computing such as scalable storage, real-time analytics, advanced machine learning capabilities, and security orchestration. The robust capabilities in the cloud infrastructure have enabled organisations to deploy and scale IoT solutions while minimising capital expenditures and operational complexities.
Amid all these technological advancements, IoT battles with some classical challenges that are tough to resolve. IoT is the convergence of information technology (IT) and operational technology (OT), it inherits the complexities from both the parent domains and also introduces new complexities related to integration, security, and governance. For example, IoT edge devices frequently operate in densely populated urban environments, remote hilly areas etc., which are challenging and also resource constrained in their own way. These devices may not have the modern features in computing, security etc. Similarly, It's not easy to manage the lifecycle of billions of devices that are on boarded onto an IoT network. For mission critical applications, major concerns arise for ensuring low latency communication and network reliability. As IoT devices may be distributed across the globe, there is a need to orchestrate a globally accepted common protocol for interoperability, compliance, scalability and need for innovation. To complicate it further, we have serious data protection regulations that vary across countries thus limiting the ability to provide cost-effective solutions.
This article brings the ten major challenges faced by IoT today and also discusses in detail about the academic research, current industry practices and real-world case studies. In each section, we discuss the specific challenge, possible solutions which will make use of the advancements in AI at the edge, lightweight protocols, edge computing, secure firmware delivery and dynamic-orchestration across cloud infrastructure. By anchoring the challenges and also aligning them with solutions, this article aims to enable the researchers, engineers and decision makers with the insights and tools that are needed to design secure, scalable and robust IoT systems that evolve rapidly with the digital ecosystem.
2. SECURITY AND PRIVACY AT THE EDGE
Challenge: Security of the devices at edge locations has become one of the critical concerns of the IoT systems. Edge devices are generally deployed in public spaces and hostile environments which are often resource-constrained and also subjected to abuse and fraud. Most of the time, these edge devices lack advanced security features like secure enclaves or hardware encryption modules and thus making them vulnerable to a plethora of attacks including firmware tampering, device spoofing, physical theft and unauthorised access. IoT networks often contain millions of connected heterogeneous devices which will increase the complexity of implementing robust security practices uniformly. All these IoT devices will not have the same communication protocols, firmware, operating systems etc., this will add more complexity to the problem. Most of the time, these IoT devices are designed with a “deploy and forget” mindset, and they are not regularly updated once they are deployed in their locations. This opens the door for an attack surface that will only increase over a period of time as vulnerabilities accumulate.
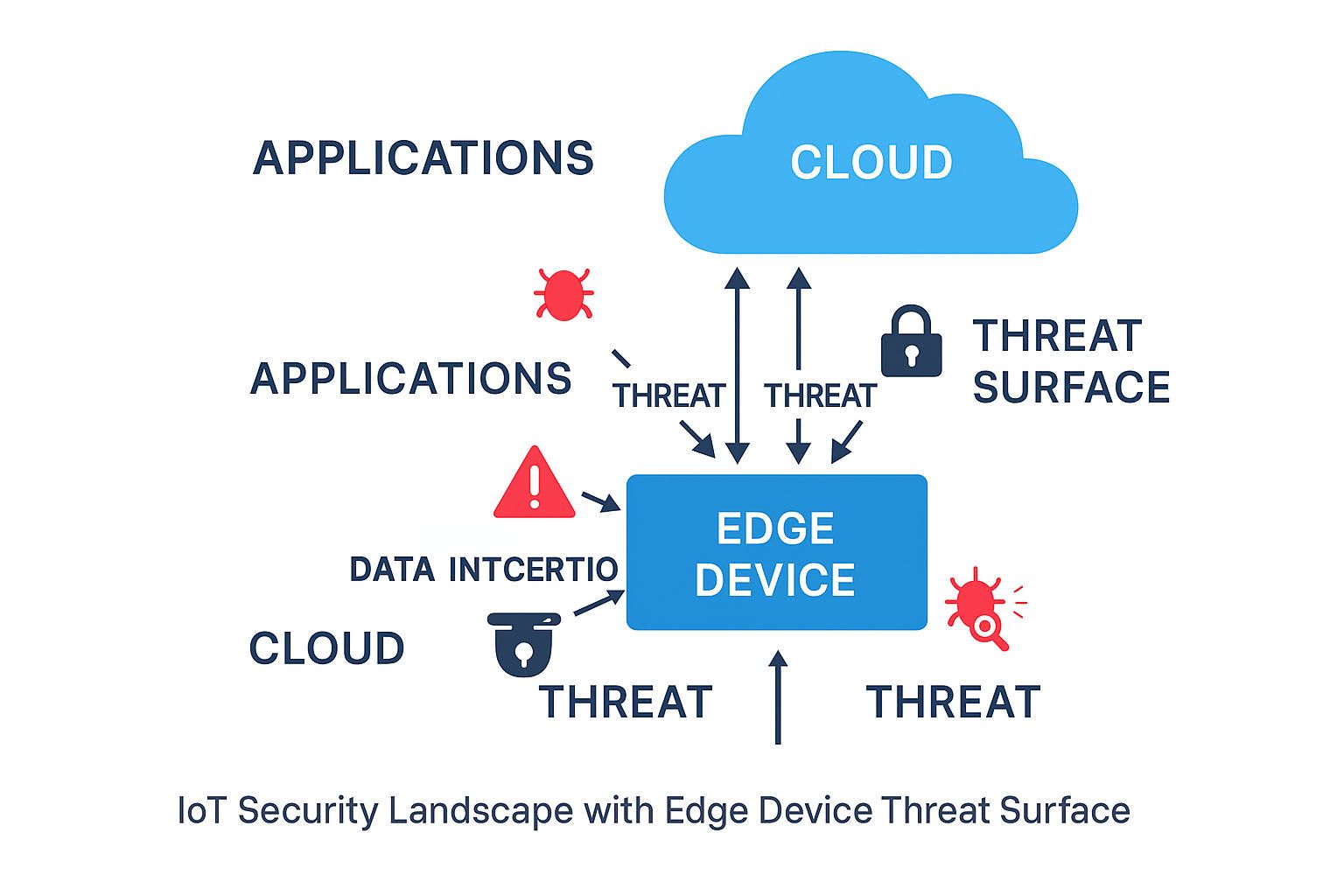
Figure 1: IoT Security Landscape with Edge Device Threat Surface
Solution: Providing security at the edge is not a straightforward approach, it needs a comprehensive and well formulated plan. To begin with, during the device manufacturing phase we must embed the devices with hardware-based security mechanisms such as Trusted Platform Modules (TPMs), secure elements and Trusted Execution Environments (TEEs). When we do this, we achieve key storage, hardware-level isolation and secure boot processes to ensure firmware integrity. Secondly, utilising the Public Key Infrastructure (PKI) and X.509 certificates we can achieve device identity and authentication. To manage device certificates and access control management, cloud platforms like AWS IoT Core and Azure Sphere have well-managed built-in tools. To achieve secure communication for low-powered devices, we can use lightweight security protocols such as Datagram Transport Layer Security (DTLS) and Constrained Application Protocol (CoAP).
Real-World Example: Tesla vehicles receive regular OTA updates including security patches via a highly secure cryptographically signed firmware. Similarly, security cameras and Nest thermostats use secure boot and encrypted communication to protect against firmware manipulation.
3. NETWORK RELIABILITY AND LATENCY
Challenge: There is an assumption that IoT applications always have seamless connectivity, but the real world deployments face varying degrees of network reliability. IoT devices that are deployed in remote areas like hilly terrains, deserts, rural areas etc., might rely on weak cellular signals, low-bandwidth wifi networks or intermittent satellite links. Latency issues and packet loss can have dire consequences for mission-critical applications like emergency response systems, telemedicine, autonomous vehicles etc. Performance can get degraded due to factors like network congestion, protocol overhead and routing inefficiencies.
Solution: Implementing edge computing is one of the most reliable and effective approaches to reduce latency. We can reduce the dependency on cloud connectivity by processing the data locally either on the device itself or at a nearby edge location. Critical data can be sent to the cloud in real-time and non-critical data gets synced to the cloud asynchronously with a small delay. To achieve deterministic networking capabilities, we have to prioritise critical traffic, enabling guaranteed delivery windows and reducing jitter etc., IEEE 802.1 group has standardised this under Time-Sensitive Networking (TSN) which is beneficial in industrial automation and vehicular networks. Protocol optimisation, dynamic bandwidth allocation and network redundancy also play a key role.
Real-World Example: Using a dense mesh of cameras and sensors with local processing, Amazon Go stores instantly detect items taken from shelves, thus creating a seamless checkout-free experience. While 5G provides ultra-reliable low-latency communication (URLLC) for critical systems, whereas technologies like LoRaWAN and NB-IoT offer low-power, long-range communication options suitable for non-latency-sensitive scenarios.
4. SCALABILITY AND INTEROPERABILITY

Challenge: By 2030, the IoT devices are projected to surpass 30 billion in number. This poses a significant challenge for managing at scale and achieving seamless interoperability. Given that IoT devices are heterogeneous, it creates a complexity to set a common standard for communication between them increasing the challenge to migrate them to cloud. As the number of IoT devices increases, it creates bottlenecks like congestion in networks, impractical firmware updates, service discovery across hostile terrain where these devices are deployed. Lack of interoperability will escalate the integration costs, fragmented data-silos and vendor lock-in for organisations. This will eventually hamper innovation, add delays to time-to-market and make it difficult to scale IoT deployments across multiple locations or business units.
Solution: By employing middleware platforms that abstract protocol-level differences and also by adopting open standards, we can achieve scalability and interoperability. For constrained environments, we need lightweight communication which can be achieved through MQTT and CoAP standards. LwM2M and mDNS protocols are highly effective for service discovery and device management. Devices, while communicating with each other should also understand the structure of the shared data. This concept is called semantic interoperability and can be achieved using ontologies like W3C’s Semantic Sensor Network (SSN). We can use middleware platforms like EdgeXFoundry and FIWARE to integrate diverse devices with cloud applications. These platforms enable seamless integration with third-party services, normalise data formats and API calls, manage device registration and status tracking.
Real-World Example: Using FIWARE, a smart city initiative in Santander, Spain deployed thousands of sensors for traffic, environment and energy management. This project illustrated how API standardization and interoperable data models enabled control across multiple domains, reducing operational silos and enabled cohesive monitoring.
5. DEVICE LIFECYCLE MANAGEMENT
Challenge: The complex and continuous task for any IoT deployment is managing the full lifecycle of devices such as onboarding, provisioning, authentication, monitoring, updates and decommissioning. Devices are generally spread across wide geographical areas and quite often exposed to environmental factors which can degrade their performance over a period of time. As we deal with thousands or millions of devices in IoT, manual device management is out of the equation and practically not feasible. If devices are not properly managed and serviced, this leads to outdated or vulnerable firmware leading to operational failures, compliance issues and even security risks.
Solution: At every stage of lifecycle management, we must integrate security into all automated processes. We can leverage scalable frameworks from cloud native platforms like AWS IoT device management, Azure IoT hub and Google cloud IoT for provisioning, authenticating, monitoring, and updating devices remotely. Using mutual authentication and hardware security modules, we can implement secure onboarding which ensures only trusted devices can join or connect to the network. Without any physical access, we can allow vendors to patch security fixes and deliver feature enhancement through OTA (Over-the-Air) firmware updates. To prevent bricking during updates, devices should be flexible to allow rollbacks and perform integrity checks. For devices which are at their end-of-life, we should have strict and secure credential revocation along with factory reset capabilities.
Real-World Example: For its industrial sensor networks, Bosch has an in-house IoT suite that enables secure onboarding and end-to-end lifecycle control. It incorporated remote-update pipelines and certificate-based authentication to reduce downtime by 40% and also significantly improve field response time to vulnerabilities.
6. ENERGY EFFICIENCY AND BATTERY CONSTRAINTS
Challenge: Most of the IoT devices generally operate in remote, harsh terrains where we have certain limitations to power supply. Sometimes, these devices have to operate for long periods after a single battery recharge. In such a scenario, there will be strict limits to the amount of data they process and also the amount of data they can transfer. This can get worse, if a situation arises where battery replacement can be cost-prohibitive or logistically challenging. As IoT systems scale, inefficient energy use can contribute to increase in operational cost, carbon emissions and electronic waste. So, the crucial goal in sustainable IoT deployments has to be balancing performance with energy efficiency.
Solution: Multiple layers of optimisation can give us energy efficiency in IoT. To enable low power consumption in sleep and active modes, we have to use ultra-low-power microcontrollers (MCUs) at the hardware level. If we can include event-driven programming models, duty cycling and adaptive sampling into the software components, it minimises unnecessary activity on the hardware side. For low power wireless transmission, certain communication protocols like Zigbee, Thread, LoRaWAN and NB-IoT are exclusively designed. Instead of using traditional approaches like pre-charged batteries, we can utilise energy harvesting technologies like small solar panels, thermoelectric generators and piezoelectric harvesters etc., These technologies have evolved to serve both fixed outdoor and high-movement mobile applications alike. To integrate harvesting circuits and optimise power distribution among components we have to utilise Power Management units (PMUs).
Real-World Example: Using a single lithium battery, Decentlab developed LoRa-based soil moisture sensors that can function for up to 10 years. These sensors can be used for smart agriculture, and they use deep sleep modes, and transmit essential data periodically thus reducing power consumption.
7. COST CONSTRAINTS

Challenge: The main barrier for startups, research institutions or developing countries to deploy IoT is the high capital expenditures that are associated with purchasing sensors, actuators, gateways and connectivity modules. Moreover, there will be operational costs for cloud infrastructure, software licensing, data storage and maintenance. All the high costs may force the organisations to compromise on security and quality of IoT functionalities, this will eventually undermine the value proposition for IoT solutions. Additionally, there will be other miscellaneous costs that will bump up the Total Cost of Ownership (TCO). If organisations lack clarity of costs and if they don't have a proper action plan, they will eventually end up with a poor risk of return (ROI).
Solution: By implementing a combination of well articulated design choice, open-source tool sets and cloud architecture optimisation we can achieve cost efficiency in IoT. Developers desire to have powerful functionality at low cost, to achieve this they opt for affordable SoCs like ESP32 or Raspberry Pi Pico at the hardware level. To ensure we have easy component swaps, it is always better to choose a modular design that’s loosely coupled. To reduce the operational costs on the software side, it is always better to choose serverless computing models that are offered by cloud computing platforms. We should also consider lightweight databases and data compression which will help us reduce data transmission and data storage charges.
Real-World Example: For monitoring soil pH, humidity and temperature, agri-tech startups in India use ESP8266 boards and GSM modules which cost under $10. These systems dramatically reduce cloud cost by transmitting minimal data via SMS or MQTT. These firms also achieved efficient and scalable solutions with minimal upfront investment by leveraging platforms like Blynk and open source firmware like Tasmota.
8. DATA QUALITY AND INTEGRATION
Challenge: In real-time and under challenging conditions, IoT systems often produce humongous volumes of data from a large set of sensors and devices. In most instances, this data is unstructured, inconsistent, redundant and noisy. Due to hardware limitations, environmental conditions and calibration drift the sensors may sometimes produce incorrect or false positive readings. In such scenarios, the downstream systems which are integrated to these IoT systems face multiple challenges while working with this data. All these together, can end up undermining the reliability of predictive models, automation systems and dashboards. This brings forth a pressing concern to organisations that do not have a robust and unified approach towards data integration.
Solution: Ensuring high-quality and reliability in data has to begin at the edge where we should focus on designing a series of preprocessing tasks such as filtering, normalisation, smoothing and deduplication of raw data before transmitting it to the cloud. To ensure consistent timestamping across distributed nodes, we should adapt Time synchronisation protocols like NTP and IEEE 1588 precision Time Protocol (PTP). Employing data lakes, middleware platforms and semantic models will address bottlenecks in integrations. Through data lakes we can achieve central aggregation based on Amazon S3 or Azure Data Lake and also edge analytics platforms like Azure Stream Analytics or Apache Edgent enable real-time pre-processing for the data. To enhance interoperability, we should use standardised data schemas such as SensorML or JSON-LD. To cleanse and harmonise datasets, it's better to use AI-based outlier detection and imputation techniques.
Real-World Example: Machine sensor data often has noise and fault prediction. To improve the accuracy of factory analytics and to reduce the noise before uploading the data to the cloud, Siemen’s MindSphere platform incorporates edge-level analytics and time-series optimisation techniques.
9. EDGE VS CLOUD PROCESSING TRADE-OFFS
Challenge: Traditional old-fashioned IoT architectures completely relied on centralised cloud infrastructures for orchestration, storage and analytics. There is a serious demand for real-time processing, data privacy, reduced bandwidth usage and operational resilience which led to the advent of edge computing. There should be a clear demarcation at the design level on which tasks should be handled at edge versus which should be done at the cloud.
Solution: A better way of handling this situation is to employ a hybrid computing approach where we perform real-time analytics, event detection and control logic at the edge nodes while the historical data analysis, machine learning model training and long-term storage are performed in the cloud. For dynamically deploying and managing workloads across edge-cloud continuum, we utilise platforms such as Azure IoT edge, AWS Greengrass and KubeEdge etc. Through model partitioning, we run components of deep learning on edge devices and the final classification and aggregation happens in the cloud. To facilitate local inference on microcontrollers, we employ lightweight AI libraries like TensorFlow Lite and Edge Impulse. It helps to define policies based on device telemetry and contextual awareness for achieving automating task migration between edge and cloud.
Real-World Example: For monitoring robotic assembly lines in real-time, BMW uses edge devices within manufacturing units. The long-term performance trends and predictive maintenance models are hosted in the cloud whereas the edge nodes are responsible for processing visual and operational data locally for immediate feedback.
10. REGULATORY COMPLIANCE AND STANDARDISATION

Challenge: Given the rapid expansion of IoT across multiple domains and regions, regulatory compliance and adherence to standards have become more sophisticated and vital. IoT systems regularly deal with mission-critical data and personal sensitive data. There are a broader spectrum of regulations that govern the storage, processing and transmission of this data. These regulations include but are not limited to the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), the Health Insurance Portability and Accountability Act (HIPAA) etc.
Solution: To start with, organisations should focus on integrating data governance frameworks and compliance checks directly into their design and operational workflows. To flag violations and enforce regulatory constraints in real-time, we should utilise automated compliance validation tools such as policy engines and privacy-by-design frameworks. To make sure the system is secure and robust, we ensure to implement strong encryption protocols, anonymisation techniques and role based access controls. To ensure that the data remains within compliant jurisdictions, we adopt geofencing and data localisation strategies. This is vital for regions where there are strict data sovereignty laws. To achieve interoperability and trust we have to adopt and align with internationally recognised standards such as IEC 62443, ISO/IEC 27001 and NIST SP 800-53 which provide a comprehensive framework to guide implementation.
Real-World Example: By adapting robust access control, audit logging and encrypted communication into its IoT-enabled medical devices, Philips Healthcare complies with HIPAA and EU MDR regulations. It utilises Azure’s compliance centre for automating assessments across more than 90 compliance certifications globally.
11. CONCLUSION
Through this article, we try to present a systematic exploration of ten persistent challenges that continue to impede scalable, secure, and sustainable IoT adoption in the cloud era. By moving beyond a survey-style narrative, we structured each challenge around technical depth, real-world relevance, and comparative solution analysis. We examined both commercial and open-source ecosystems to address areas including device lifecycle automation, semantic interoperability, energy optimisation, and edge-cloud orchestration. Case studies such as Bosch’s remote firmware control and FIWARE’s smart city deployment provided applied context. A key contribution from this article is its integrated challenge-solution taxonomy, which can help architects and engineers map technology choices to real-world constraints such as bandwidth, cost, and regulatory limits. Additionally, the emphasis on lightweight protocols, hybrid AI pipelines, and compliance frameworks offers a grounded perspective on evolving system design practices. For instance, privacy-by-design models and automation-ready regulatory enforcement mechanisms are necessary to align with mandates like GDPR and HIPAA.
To advance the field, we propose three future research priorities:
- Self-healing IoT middleware that supports autonomous device recovery, version rollbacks, and decentralised orchestration.
- Standardised energy and latency benchmarks for evaluating edge devices in variable real-world conditions
- Open, modular frameworks that reduce vendor lock-in and promote cost-effective deployments for startups and public sector projects.
In bridging academic insight and enterprise-grade applicability, this work aims to contribute a roadmap for resilient and future-proof IoT ecosystems—systems that not only scale technologically, but also uphold security, interoperability, and global compliance as core design principles.
Author Bio
Satya Karteek Gudipati is a Principal Software Engineer based in Dallas, Texas, with over 15 years of experience in full-stack development, cloud computing, and AI-driven systems. He has led enterprise-scale implementations across sectors including eCommerce, telecom, and customer service automation. His recent work focuses on Generative AI, multi-agent chatbot architectures, and intelligent IoT integration. Satya actively contributes to peer-reviewed research and industry forums, aiming to bridge the gap between academic innovation and enterprise adoption. He holds a Master’s degree in Computer Science from Arizona State University and regularly publishes technical papers in IEEE, Springer, and other reputed outlets. You can reach out to Satya on LinkedIn.
REFERENCES
[1] Palattella, M. R. et al. (2023). "Energy-efficient networking for IoT."
[2] Dutta, P., Culler, D. (2022). "Green IoT: An energy-efficient architecture."
[3] Lin, J. et al. (2023). "Cost optimization in large-scale IoT applications."
[4] Bonetto, R. et al. (2023). "Open-source ecosystems for cost-efficient IoT innovation."
[5] Zhang, Y. et al. (2022). "Data preprocessing for edge-enabled IoT systems."
[6] Li, J., Chen, T., & Wang, S. (2023). "Integration challenges and solutions in IoT data streams."
[7] Lane, N. D., Bhattacharya, S., & Georgiev, P. (2023). "TinyML: Machine learning on edge devices."
[8] Varghese, B., & Wang, N. (2022). "Edge-cloud synergy in IoT architectures."

Love My Online Marketing has 10+ Years of working alongside businesses and helping them grow. Discuss your options for online success from website Design and Development through to Google Marketing.
Do you want more traffic and business leads?
Love My Online Marketing is determined to make a business grow. Our only question is, will it be yours?